Wireless companies would love to charge each app a different fee to access the Internet.
Source: Imagine a world where every app has its own data plan | Ars Technica
Wireless companies would love to charge each app a different fee to access the Internet.
Source: Imagine a world where every app has its own data plan | Ars Technica
Senator Al Franken says net neutrality rules that exempt wireless broadband and permit paid prioritization could cause “more harm than doing nothing at all.”
Source: Senator: New net neutrality plan worse than “doing nothing at all” | Ars Technica
If you haven’t written your congressmen about this yet, this is about your last chance to do so. Given the difficulty and rarity of serious changes to federal policies, you are going to have to live with the results for the rest of your lives.
Amazon has reportedly begun removing content that touches on various forms of incest—from both its online store and buyers’ Kindles.
Source: Amazon’s latest Kindle deletion: erotic, incest-themed fiction | Ars Technica
It’s the “big brother” aspect of this that bothers me the most.
IT spending has hollowed out labour markets, to the detriment of middle-income workers
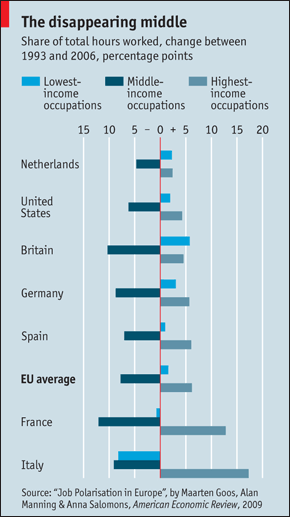
Source: Automatic reaction | The Economist
Not surprising by itself, but it is nice to have some numbers to confirm what I (and I suspect most other people) had suspected about the effects of IT on the job market.
I wonder where IT workers fall in the low-middle-high income scale.
Do you need antivirus software on your PC? If you’re not sure of the answer to that question, then the short answer is yes. The longer answer is that security software is only one piece of what should be a simple, straightforward, and systematic approach to your PC’s health. Here’s my seven-step program.
Source: Do you really need antivirus software? | ZDNet
My favorite part of this is that people are mostly getting infected by malware exploiting vulnerabilities that were patched 2-3 years ago (but YOU keep ALL the software on your computer updated, right?) and the rest of the top-10 most common are installed through social engineering. There is no software or hardware that provides security against the user’s ignorance or gullibility.